There is always some new attack vector in crypto. A new one is Bitcoin Address Poisoning.
In the context of Bitcoin addresses, attackers can mimic a victim’s address by creating addresses that are visually similar or have similar patterns.
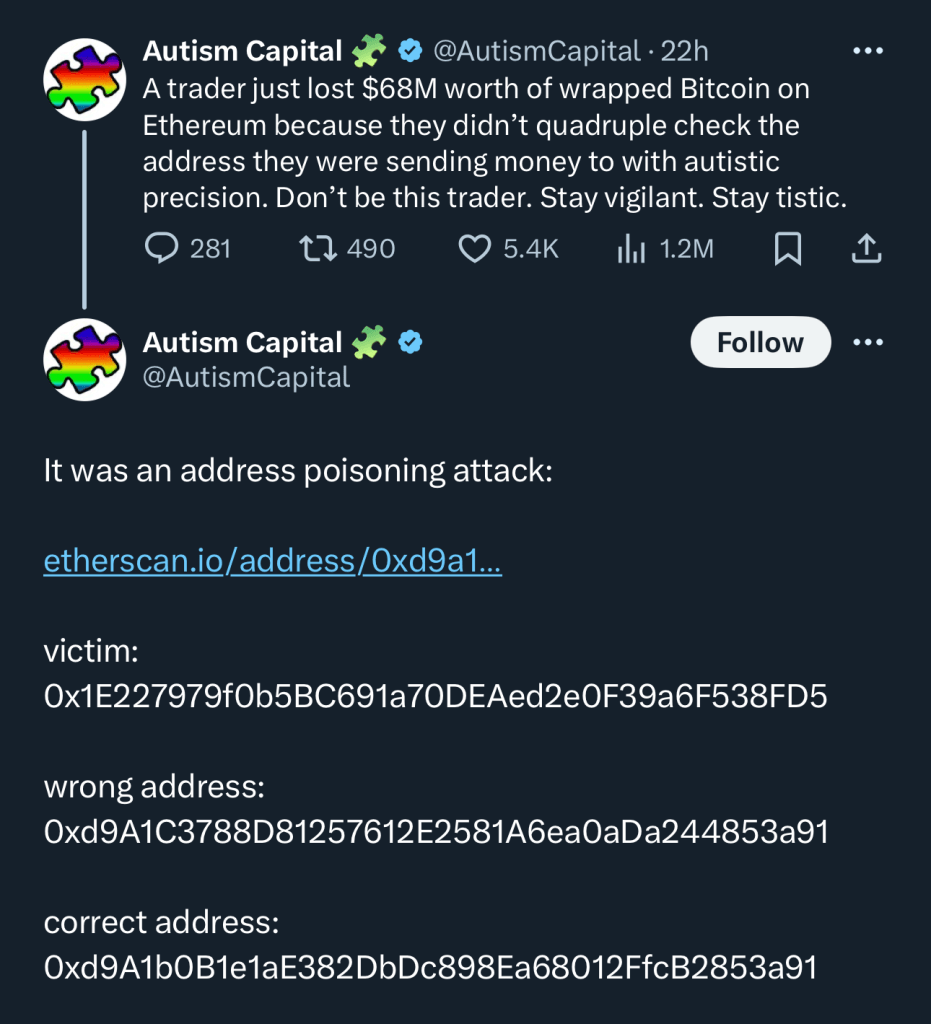
Attackers may add or remove characters from the address, especially if the victim’s address is long. They might add extra characters or remove some characters to make the address appear similar.
Attackers can use a trial-and-error approach, generating a large number of addresses and checking for similarities with the victim’s address.
Here are the steps attackers might follow to create a Bitcoin address similar to a victim’s address:
- Identify the Victim’s Address: Attackers start by obtaining the victim’s Bitcoin address. This could be through various means such as social engineering, phishing, or by monitoring public transactions associated with the victim.
- Analyze the Address Format: Bitcoin addresses follow a specific format and structure. Attackers analyze the victim’s address to understand its format, including the length, characters used, and any patterns or common elements.
- Choose a Similar Address Format: Based on the analysis, attackers choose a format for the similar address. This could involve deciding on the length, the type of characters (e.g., alphanumeric), and any patterns they want to mimic.
- Generate Similar Addresses:
- Character Substitution: Attackers use tools or scripts to substitute characters in the victim’s address with visually similar ones. For example, “1” can be substituted with “I” or “0” with “O”.
- Transposition: Tools can also be used to swap adjacent characters in the address to create variations.
- Adding/Removing Characters: Attackers add extra characters or remove some characters while maintaining the overall format and pattern of the address.
- Prefix/Suffix Matching: Attackers create addresses with the same prefix or suffix as the victim’s address and then modify the remaining characters to match their chosen format.
- Check for Similarity: After generating a list of similar addresses, attackers check each one against the victim’s address to see if there are any matches or close resemblances.
- Testing and Refinement: Attackers may test the generated addresses in various scenarios, such as sending small amounts of cryptocurrency to see if transactions go through. They may refine their approach based on the results and feedback from these tests.
Examples of general types of tools and platforms that attackers might use:
- Phishing Platforms:
- PhishLabs
- SocialFish
- Evilginx
- Spoofing Tools:
- Email spoofing tools (various open-source and commercial options)
- Caller ID spoofing services
- Domain spoofing scripts
- Brute Force Tools:
- BTCGen
- Bitcoin Vanity Address Generator (can be misused for malicious purposes)
- Custom Python or JavaScript scripts for address generation
- Social Engineering Kits:
- HiddenEye
- SEToolkit (Social-Engineer Toolkit)
- SETOOLKIT (similar to SEToolkit but with additional features)
- Data Gathering Tools:
- Maltego
- Shodan
- OSINT Framework (collection of various tools for OSINT)
- Cryptocurrency Mixers/Tumblers:
- CoinMix
- Blender.io
- ChipMixer
Please note that while some of these tools have legitimate purposes (like OSINT tools for gathering publicly available information), they can also be misused by attackers for malicious activities such as social engineering attacks or generating similar Bitcoin addresses.
Users should always double-check the entire Bitcoin address before sending funds, especially when dealing with large transactions or unfamiliar addresses. Using QR codes from trusted sources can also reduce the risk of address mimicry in social engineering attacks.




Leave a comment